Signature Authorization
About 2 min
Digital Signature Overview
Digital signature authentication is a critical security mechanism for all API transactions, including Pay-In, Pay-Out, and Inquiry operations (inquiry status and inquiry balance). This process ensures request integrity, authenticity, and non-repudiation through cryptographic verification.
Signature Generation Process
Step 1: Prepare Signature Data
Gather the following components for signature generation:
- X-TIMESTAMP: ISO 8601 formatted timestamp
- Merchant Secret: Your assigned merchant secret key
- Request Body: JSON payload (will be minified)
- Merchant Private Key: Your RSA private key for signing
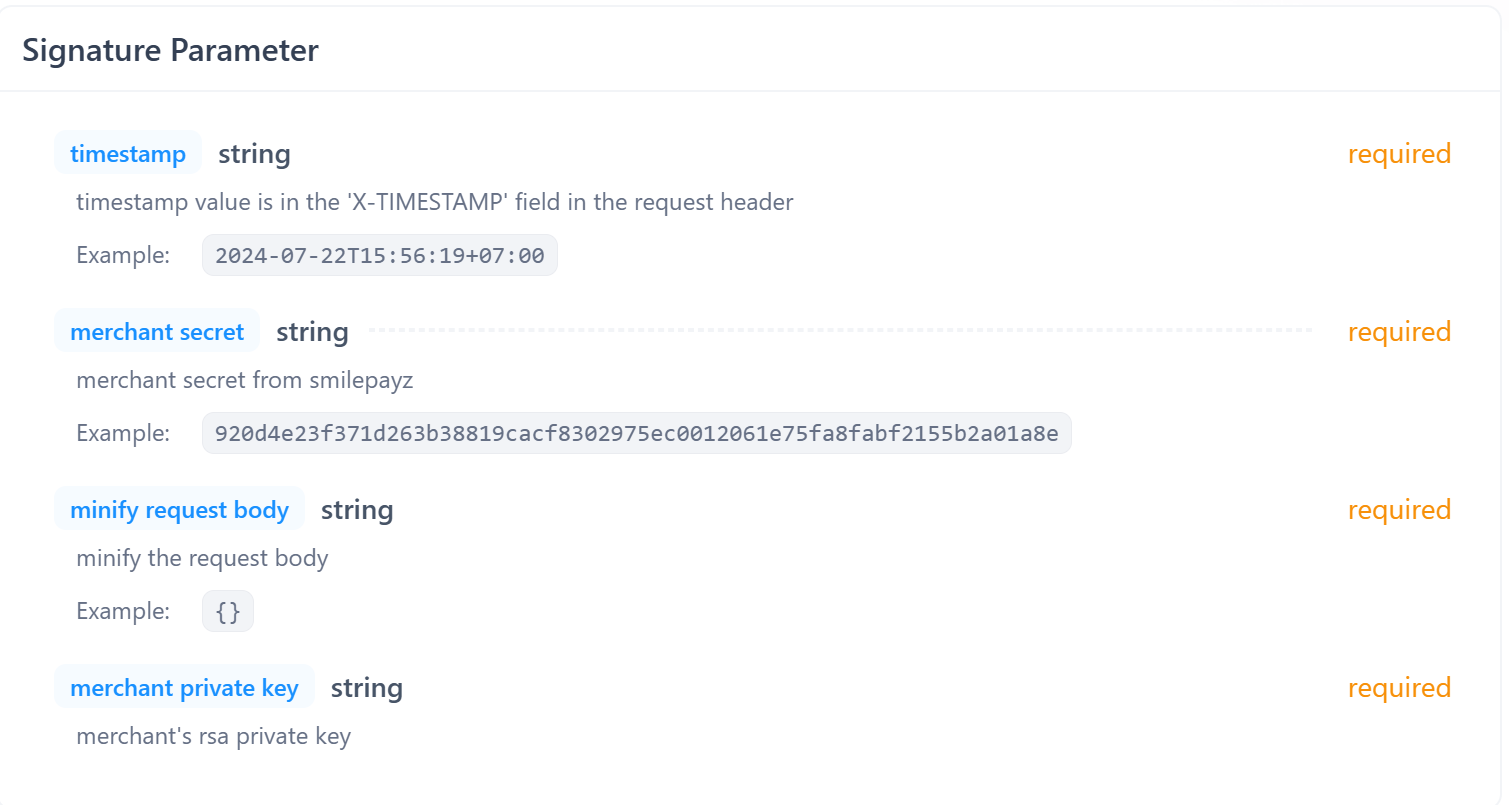
Step 2: Minify Request Body
Remove all unnecessary whitespace and formatting from the JSON request body to ensure consistent signature generation.
Before Minification:
{
"additionalParam": {},
"area": 10,
"callbackUrl": "https://docs.smilepayz.com/en/",
"merchant": {
"merchantId": "20019"
},
"money": {
"amount": 10000,
"currency": "IDR"
},
"orderNo": "20019c5b63c4b-e34a-4855-9b20-d4b",
"paymentMethod": "QRIS",
"purpose": "Purpose For Transaction from Java SDK"
}
After Minification:
{"paymentMethod":"QRIS","orderNo":"20019c5b63c4b-e34a-4855-9b20-d4b","purpose":"Purpose For Transaction from Java SDK","additionalParam":{},"money":{"currency":"IDR","amount":10000},"merchant":{"merchantId":"20019"},"callbackUrl":"https://docs.smilepayz.com/en/","area":10}
Step 3: Compose String to Sign
Create the signature string by concatenating the components with pipe separators:
X-TIMESTAMP + "|" + merchant_secret + "|" + minify(requestBody)
Example String to Sign:
2024-12-30T18:30:36Z|95b57c46b8c2e068982be23fb669a80612cad68e6ce6ba4f5af9ec20d23bb274|{"paymentMethod":"QRIS","orderNo":"20019c5b63c4b-e34a-4855-9b20-d4b","purpose":"Purpose For Transaction from Java SDK","additionalParam":{},"money":{"currency":"IDR","amount":10000},"merchant":{"merchantId":"20019"},"callbackUrl":"https://docs.smilepayz.com/en/","area":10}
Step 4: Generate Digital Signature
Apply SHA256withRSA encryption to the signature string using your RSA private key.
Cryptographic Formula:
SHA256withRSA(stringToSign, merchantPrivateKey)
Example RSA Private Key:
MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC1d8Zaurk/A0WB1X7CrW+SqsVM4v2ZMGTdqWEQOAKQyY/DZEmgSm7whUMLYfqeKxzzAd3lZHvviyO/V/Ht2i8axtiA5tyDa485IgBy+jO9UHxzI+9CRxnIY5jjDAqAgEvRa0HZEfYHLGlH3IQ4A2a7g8Wm3yqn2prIrgY21nO4+33GuBR0qCpGxth0kV7/RSdhWv3Ff1zkb7yUYn9zfuag9stLf1nw+Ui7hjXL+xGiNRYsDCHOLzKynZxk1cBfqyPY5YMTIjQik4cI+YfM4BMN8bmTB1y3z9sdfbHVTI/PD/fbDzvfK7S/XJvY2bj1TwNeYCHcd5Dx6MYiO12rfA5XAgMBAAECggEASRpMJMat042c1ZXM793wYXQ78SJMKQcOyyDtwhveJLeeG4duBY2WrXvxq0c4L7mMevSYkE1vg+tYZj+mbTwE19Oc6iiWUrbkxo5FAgx7BVvEFpo2S0vbPhepQmXaYTPN1zpPF4QdyXwBmXpjJTFxlD6cRAII6/+rdQZt6G9xxOWUq6bbENNUc6y+N+97oPPwrzLZGYADfusM735Mlx3j8xTGLSHTh2d8e5epwKcSW+ZvBbiM30ZeO+M5bh6zgZrHpPQNJAOsEDuVk5vjuC5O+i81YwP702GAE50zI9Ysr4QMS3QQGe2jwpJAmMjvO6/MRv/6De83NJ6Y70+00OONcQKBgQDtP+sQOyKRErCN9ePmu6FBfzMZcTC5vXQpA0kW7vUMKyQR537appYcOb5DPJDgUqqyNcr8vIqadR6OW0thkfRyb+L/elOyS/XnVbFc6RA9DW/KV4xm68LUX9oRqfgy5YOESEEA2igEh8IdqfkIRCZ3g7xrQUmb3gq0BM2/hnxyHwKBgQDDz0Slbw2Pv820CSheZi8HQf3sEFe0JDHKo2KAHX9rTvFEF3xsT+UZh6pcHUcesYlVlJM2Ciejq4dmiOnvGIKtkqtcLfioVbPrDP2HlDtIT3mSC7sL6VdWLxYz/l0EVjsR2KMVwXD42jcjz3e5bDIi98Z8G4Bx6cu6pwlBtfMMyQKBgHJhWoacu/GNPSlz3sgitX/KP2yIsaEawaH0P4ya7/FJ6z3mibYIkl5RSHVKAd7ke/8nCBIJJBmLVYv0X8dOgreZUasx4qAXFxrMqZHNm1KT4819n+cOywNwosXZWBvRozJnU0+B3cExYljC1ZkyogkErhZXh5Fp32ci2b74q46pAoGANWyixSRkpdjmLf3lpsPohulpd3QKCdtqPmiPonbp4gRa7YIe74po7qtGPvW6BtTXrKLp+2+P2yccvUwTz6l3VhZTbMYaNwuTGEmmDszR0+vjNoa+1QQoURpty2fWRy2j1j2uWWw6/5rCOqILf2rWzxWdcRUr2Wi5rkaOzv/uvYkCgYEAlFV6huNhi1NIIg5gkTS0kmxnIUWu8XIT9IgZWMrhR7TvImVISoormE9LdISgMBz+J5YJxhAZbxVxlUJrsl+HVcS81gmUkeoIpTA+iKUzbD9gAPjEdqVylzN8A9uNIkkb5Cf4BWYfEyMaLfBuiHDlKDcBjz4cJbcom3RVGacghKc=
Generated Signature Example:
RvWeMDztovywfyarzFEUUDUo6F5f0weT+X2FTfjJ/KVxyDJJ4PHddsqHx0h98/ZOofCaADx8MaoG1rTaHd+5BkJPPlwrwG62oZygjNOV2gJ0rstTBWZOQgORkTjvBj91KQgzWRpT6yLJaeRaJRS2YfRPGA5MH7ieGWkocPXNRw+v0HolPMren+y69sZmVVXeRs9SXV9QpCZP8zNHPEQt75zgVKSr5/GmkfTCgFPNz/+23MpVMigwpOcifxEDwN+KzfdnQxjYi6n01qztb1skXOTlIRrhDkJSRhOzrDHQEwnp/6XEjyZaOV/XXSJtMsr85Yl97cF0daW1ALkuF7NHew==
Step 5: Include Signature in HTTP Header
Add the generated signature to the HTTP request header:
X-SIGNATURE: RvWeMDztovywfyarzFEUUDUo6F5f0weT+X2FTfjJ/KVxyDJJ4PHddsqHx0h98/ZOofCaADx8MaoG1rTaHd+5BkJPPlwrwG62oZygjNOV2gJ0rstTBWZOQgORkTjvBj91KQgzWRpT6yLJaeRaJRS2YfRPGA5MH7ieGWkocPXNRw+v0HolPMren+y69sZmVVXeRs9SXV9QpCZP8zNHPEQt75zgVKSr5/GmkfTCgFPNz/+23MpVMigwpOcifxEDwN+KzfdnQxjYi6n01qztb1skXOTlIRrhDkJSRhOzrDHQEwnp/6XEjyZaOV/XXSJtMsr85Yl97cF0daW1ALkuF7NHew==
Signature Verification
RSA Public Key for Verification
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAtXfGWrq5PwNFgdV+wq1vkqrFTOL9mTBk3alhEDgCkMmPw2RJoEpu8IVDC2H6nisc8wHd5WR774sjv1fx7dovGsbYgObcg2uPOSIAcvozvVB8cyPvQkcZyGOY4wwKgIBL0WtB2RH2ByxpR9yEOANmu4PFpt8qp9qayK4GNtZzuPt9xrgUdKgqRsbYdJFe/0UnYVr9xX9c5G+8lGJ/c37moPbLS39Z8PlIu4Y1y/sRojUWLAwhzi8ysp2cZNXAX6sj2OWDEyI0IpOHCPmHzOATDfG5kwdct8/bHX2x1UyPzw/32w873yu0v1yb2Nm49U8DXmAh3HeQ8ejGIjtdq3wOVwIDAQAB
Development Tools
JSON Minification Tools
| Tool | URL | Usage |
|---|---|---|
| JSON Formatter | https://jsonformatter.org/json-minify | Select "Minify JSON" option |
Security Best Practices
Key Management
- Secure Storage: Store private keys in secure, encrypted storage
- Key Rotation: Regularly rotate RSA key pairs
- Access Control: Limit access to private keys to authorized personnel only
- Backup: Maintain secure backups of private keys
Implementation Guidelines
- Timestamp Accuracy: Ensure X-TIMESTAMP is within ±5 minutes of server time
- Request Integrity: Never modify request body after signature generation
- Error Handling: Implement proper error handling for signature validation failures
- Logging: Log signature generation attempts for audit purposes
Common Issues and Solutions
- Signature Mismatch: Verify all components are in correct order and format
- Timestamp Issues: Ensure system clock is synchronized with NTP servers
- Key Format: Verify RSA key format and encoding
- Encoding Issues: Ensure proper UTF-8 encoding for all string components
Compliance and Standards
Cryptographic Standards
- Algorithm: SHA256withRSA (SHA-256 hash with RSA signature)
- Key Size: Minimum 2048-bit RSA keys recommended
- Encoding: Base64 encoding for signature output
- Format: PKCS#8 format for private keys
Audit Requirements
- Signature Logs: Maintain logs of all signature generation and verification
- Key Usage: Track key usage and rotation schedules
- Access Logs: Monitor access to cryptographic materials
- Compliance Reports: Generate compliance reports for regulatory requirements
